Subtotal $0.00















Stay ahead of attackers with integrated feeds from global phishing advisories. Instantly simulate the latest real-world threats in your awareness campaigns.

Stay ahead of attackers with integrated feeds from global phishing advisories. Instantly simulate the latest real-world threats in your awareness campaigns.
Simulate phishing, spear-phishing, vishing, smishing, and even deepfake scams. A broad coverage ensures employees are trained for all possible attack types.


Simulate phishing, spear-phishing, vishing, smishing, and even deepfake scams. A broad coverage ensures employees are trained for all possible attack types.

Combine phishing simulations with full-scale incident response drills. This tests both employee vigilance and organizational response readiness.

Combine phishing simulations with full-scale incident response drills. This tests both employee vigilance and organizational response readiness.
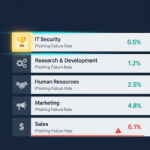
Encourage teamwork and competition by tracking phishing resilience at the department level. Leaderboards make awareness initiatives measurable and fun.


Encourage teamwork and competition by tracking phishing resilience at the department level. Leaderboards make awareness initiatives measurable and fun.
Build role-specific awareness journeys for different departments or risk levels. Customization ensures training is relevant and impactful for every employee.

Build role-specific awareness journeys for different departments or risk levels. Customization ensures training is relevant and impactful for every employee.
Regular refresher sessions to keep security knowledge up to date. Automated reminders ensure employees don’t forget critical practices over time.


Regular refresher sessions to keep security knowledge up to date. Automated reminders ensure employees don’t forget critical practices over time.

Short, engaging videos that educate employees on identifying and avoiding phishing attacks. Visual learning improves retention and effectiveness.

Short, engaging videos that educate employees on identifying and avoiding phishing attacks. Visual learning improves retention and effectiveness.
Professionally designed posters that deliver bite-sized security tips. Placed in common areas, they reinforce phishing awareness daily.


Professionally designed posters that deliver bite-sized security tips. Placed in common areas, they reinforce phishing awareness daily.

Generate compliance-ready audit logs and detailed awareness reports. These provide management and regulators with clear evidence of security readiness.

Generate compliance-ready audit logs and detailed awareness reports. These provide management and regulators with clear evidence of security readiness.
Link simulations with the organization’s IR playbooks to test detection, escalation, and response. Teams gain hands-on experience in handling real phishing incidents.

Link simulations with the organization’s IR playbooks to test detection, escalation, and response. Teams gain hands-on experience in handling real phishing incidents.

Extend cybersecurity awareness to employees’ families through simple guides and training. This reduces the risk of home-based attacks that can spill over into the workplace.

Extend cybersecurity awareness to employees’ families through simple guides and training. This reduces the risk of home-based attacks that can spill over into the workplace.
Deploy engaging awareness posters across offices and integrate training with Learning Management Systems. This ensures a seamless and consistent learning experience for all employees.


Deploy engaging awareness posters across offices and integrate training with Learning Management Systems. This ensures a seamless and consistent learning experience for all employees.
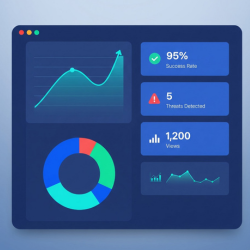
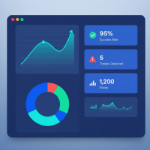
Monitor phishing simulations and awareness campaigns with real-time dashboards. Visual reports highlight high-risk users, trending vulnerabilities, and overall security posture.

Monitor phishing simulations and awareness campaigns with real-time dashboards. Visual reports highlight high-risk users, trending vulnerabilities, and overall security posture.
Prepare your workforce for modern threats by simulating AI-powered deepfake calls and videos. Employees learn to identify and report sophisticated impersonation attacks.


Prepare your workforce for modern threats by simulating AI-powered deepfake calls and videos. Employees learn to identify and report sophisticated impersonation attacks.
Continuous, subscription-based awareness campaigns tailored to your organization’s threat landscape. Regular updates ensure employees are always trained on the latest attack techniques.

Continuous, subscription-based awareness campaigns tailored to your organization’s threat landscape. Regular updates ensure employees are always trained on the latest attack techniques.
Make awareness training fun and engaging with points, badges, and leaderboards. Healthy competition motivates employees to actively participate and improve their phishing resilience.


Make awareness training fun and engaging with points, badges, and leaderboards. Healthy competition motivates employees to actively participate and improve their phishing resilience.

Identify security-conscious employees and empower them as “Cyber Champions.” They act as peer mentors, spreading awareness and building a culture of security within departments.

Identify security-conscious employees and empower them as “Cyber Champions.” They act as peer mentors, spreading awareness and building a culture of security within departments.

